PowerClerk Support Center
- Program Design
-
- Automations
- Channels
- Communications
- Connections
- Content Library
- Custom API IDs
- Data Fields
- Deadlines
-
- Questions to ask yourself
- Locating the Deadlines feature
- What are Deadlines
- How to Create a Deadline
- Deadline Automation Action Rules
- Utilizing Project Admin Page for Deadlines
- Communication Templates for Deadlines
- Deadline Set/Satisfy Options
- Program-Wide Deadline Actions
- Reporting on Deadlines
- Deadlines in Project List Columns
- FAQs
- Document Templates
- eSignature Envelopes
-
- Questions to Ask
- Locating the eSignature Feature
- What are eSignature Envelopes?
- eSignature Checklist: The Prerequisites to create a new Envelope
- How to set up Advanced eSignature Envelopes Step-by-Step
- How to add an eSignature Envelope to a form
- eSignature Automation Trigger
- Viewing Completed eSignature Envelopes
- Resending eSignature Notifications
- Canceling eSignatures
- FAQs
- Forms
- Formulas and Calculated Fields
- Front Page
- Incentive Design
- Milestones
- Project List Columns
- Project Summary
- Project Views
- Roles
- Workflow
- Administration
- Tools Menu
- Integration Guides & API
- PowerClerk Video Guides
-
- New User Video Guide
- Setting up Business Days
- Dashboards
- FormSense
- Edit Forms - Tutorial #1
- Calculated Fields
- Build A Formula
- Milestones
- Edit Forms - Tutorial #2
- Project Summary
- Automation with Formulas in Action Rules
- Setting up Roll-up Reports
- Configuring Forms
- Roles and User Administration
- Formulas and Advanced Visibility Rules
- Visualize Workflows
- ArcGIS
- API
- SFTP Automatic Data Import
- Standard Web Adapter Setup
- PowerClerk Program Launch
- PowerClerk User Group Sessions (UGS)
- Learning Management System (LMS)
- Join us for Reflow!
- NEW: PowerClerk Certifications
Single Sign On (SSO)
SSO provides added security and improves the login experience for utility program administrators. When admins are logged on to their internal networks, they can access PowerClerk without having to log in again.
PowerClerk SSO Configuration
Single sign-on (SSO) is a session and user authentication service, which allows a user to create only one set of login credentials to access multiple applications. The service authenticates the end user for all the applications the user has been given rights to and eliminates the need to further prompt the user when switching applications during the same session.
Please note: SSO is available as an additional feature for PowerClerk (like web adapters). Please contact your PowerClerk Account Executive if you would like to add the SSO feature to your program. Implementing your SSO solution is possible with a variety of identity providers (IDPs). For example you can use the services of the following IDPs:
- Azure Active Directory (AD) (https://azure.microsoft.com/en-us/services/active-directory/)
- Okta (https://www.okta.com/)
- onelogin (http://www.onelogin.com/)
- JumpCloud (https://jumpcloud.com/)
Before you begin configuration, make sure that you have a user account for the PowerClerk program you intend to configure. This will allow you to properly test the configuration, including the SAML responses.
The remainder of this webpage describes how to set up SSO for a PowerClerk program. The setup requires creating and configuring an application within your IDP. Also, certain information must be provided to CPR to configure PowerClerk as the Service Provider (SP). The sections below provide directions for configuration through Azure AD and Okta.
Azure AD Configuration (SAML)
To configure Azure AD for PowerClerk, follow the steps outlined in the following Microsoft tutorial:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/configure-single-sign-on-non-gallery-applications.
In Step 1.6, the “Identifier (Entity ID)” needs to be configured is as follows:
- Sandbox: https://<program_name>.cleanpowerdemo.com/PCITrial/
- Production: https://<program_name>.powerclerk.com/
…and the “Reply URL” is:
- Sandbox: https://<program_name>.cleanpowerdemo.com/PCITrial/MvcAccount/Login/Acs
- Production: https://<program_name>.powerclerk.com/MvcAccount/Login/Acs
[where program_name is the host name of the PowerClerk program, found in the browser URL].
Please note: the other three (3) settings in Step 1.6 (i.e. Sign-on URL, Relay State, Logout URL) *do not* need to be configured (i.e. they should be left blank).
In Step 2, the following five (5) attributes need to be configured:
- FirstName
- LastName
- UserId
- PowerClerkRoles (optional)
Please note: Within Azure >> Entra administrative interfaces, please ensure any optional Attributes and Claims >> Namespace fields are left unset and empty.
The optional PowerClerkRoles attribute will contain the name of the role in PowerClerk that the user should be assigned to (look to Figure 7 of the Okta configuration, below, for an example). This attribute may be omitted by setting up a default role that will automatically be assigned to new users, reach out to your PowerClerk representative to configure. See the following link for details on setting up application-defined roles:
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-enterprise-app-role-management
If you are unsure on what roles need to be set up on your side, either 1.) ask your internal colleagues who are administering the PowerClerk program, or 2.) log in to PowerClerk and navigate to Program Design > Roles. If you don’t have a PowerClerk account, please request one from an internal colleague that has a PowerClerk user account with administrative privileges.
Please note: Azure AD will give an error when the role called “Program Designer” has a space in between “Program” and “Designer”. The workaround is to rename the role (in both PowerClerk and Azure AD) to a naming convention similar to the following examples: “ProgramDesigner”, “Program-Designer”, or “Program_Designer”.
From Step 3, CPR needs to be given the SAML Signing Certificate (click the blue “Download” hyperlink for “Certificate (Base64)”). Please note: never send us your private Certificate key, only the public key. Please ensure that the SAML Signing Certificate provided is trusted by a public Certification Authority (CA).
From Step 4, CPR needs to be given the “Login URL” and “Azure AD Identifier“.
Azure AD Configuration (OIDC)
To configure Azure AD as an OIDC provider to use with PowerClerk, follow the steps in the following Microsoft tutorial: https://learn.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
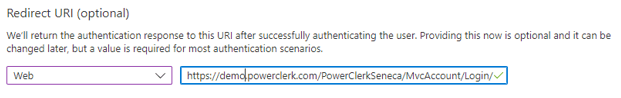
When setting up redirect uris, use values as follows:
- Sandbox: https://<program_name>.cleanpowerdemo.com/PCITrial/MvcAccount/Login/OAuth2Redirect
- Production: https://<program_name>.powerclerk.com/MvcAccount/Login/OAuth2Redirect
In Token Configuration, add the following claims to the access token:
- family_name
- given_name
Click Manifest:

Set accessTokenAcceptedVersion to 2. Click Save. Click Expose an API:
Add a scope, give it a name to inform users the permissions they are giving to PowerClerk (email, first, and last name). Share the scope name with your PowerClerk representative, something like “api://00000000-0000-0000-0000-000000000000/PowerClerk”
Under Certificate & Secrets, create a Client Secret, share the value with your PowerClerk representative, along with the Client Id.
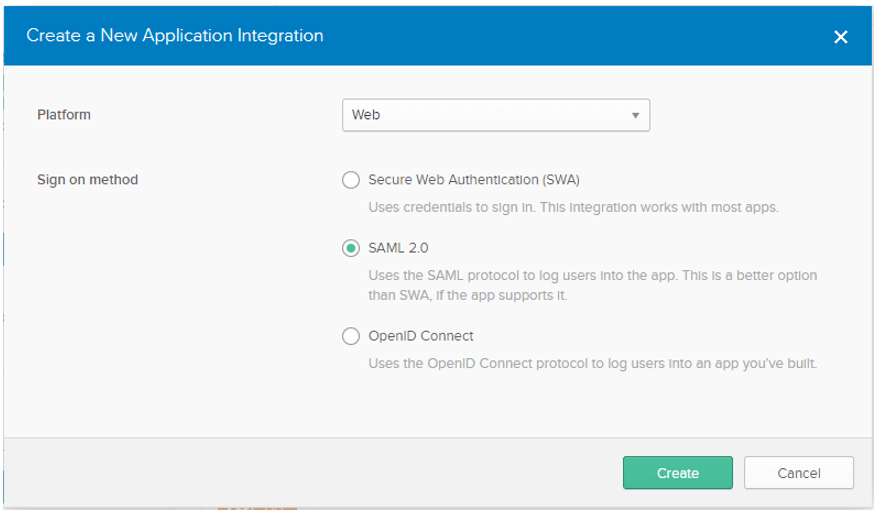
Okta IDP Configuration (SAML)
Create a new application in Okta and choose SAML as the sign on method.
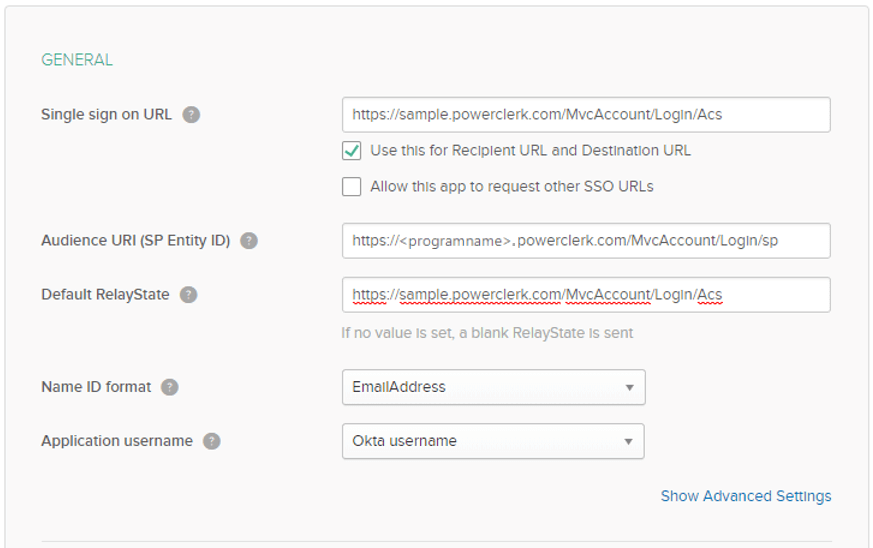
In Figure 5, below, the Single sign-on URL and Default RelayState, need to be configured as follows:
- Sandbox: https://<program_name>.cleanpowerdemo.com/PCITrial/MvcAccount/Login/Acs
- Production: https://<program_name>.powerclerk.com/MvcAccount/Login/Acs
[where program_name is the host name of the PowerClerk program, found in the browser URL].
and the “Audience URI (Entity ID)” is:
- Sandbox: https://<program_name>.cleanpowerdemo.com/PCITrial/
- Production: https://<program_name>.powerclerk.com/
…and for the “Name ID format” select “EmailAddress”.
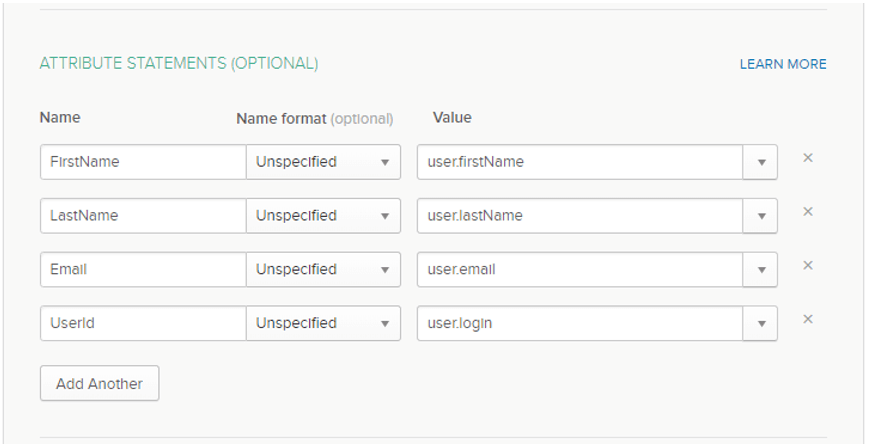
Add 4 entries to the Attribute Statements section for the first name, last name, email, and user id, as shown below:
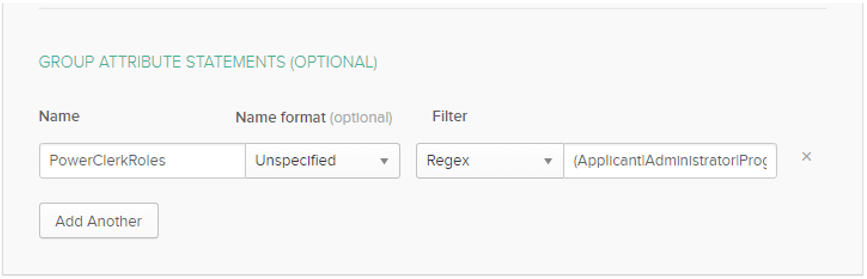
If you are using IDP-configured roles, add 1 entry to the Group Attribute Statements section with the name “PowerClerkRoles”. This will be a regular expression which selects Okta Group Names to pass to PowerClerk to use as the Role. For example, if the PowerClerk Roles are Administrator, Applicant, and Program Designer, the regular expression would be “(Applicant|Administrator|Program Designer)”. Each user must belong to exactly 1 Okta group which has a name that matches the name of a Role in PowerClerk.
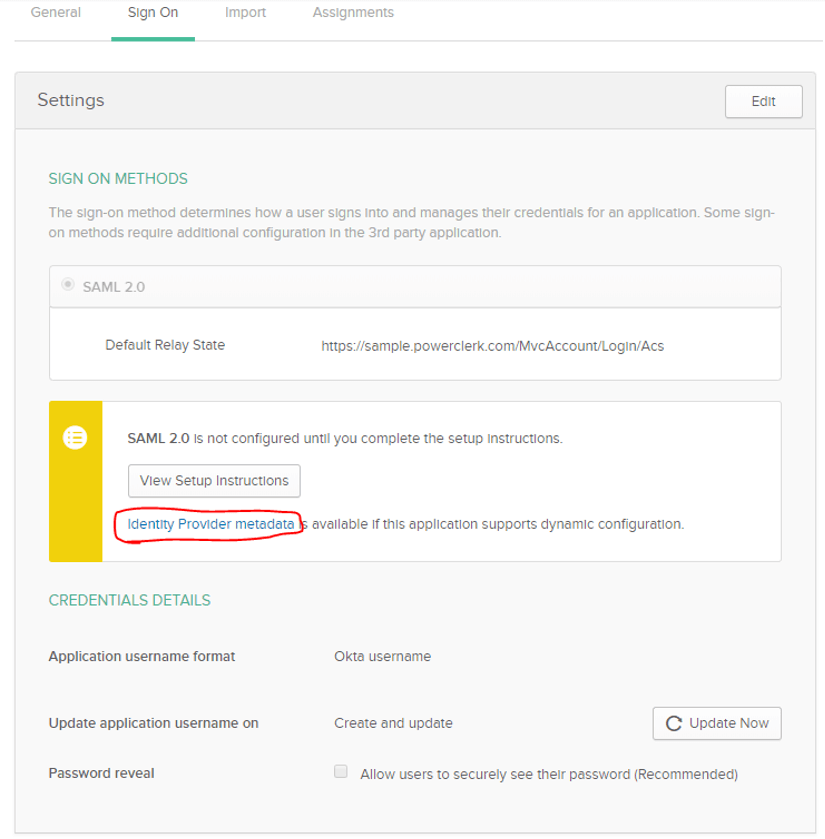
SP Configuration
After creating the Okta application, click the “Identity Provider metadata” link in the Settings section. This will generate an XML file that should be sent to CPR. The XML contains the data required to configure PowerClerk to communicate with the IdP application.
By default, if a user is not logged in, the front page in PowerClerk will show a link to Okta’s login page. After logging in through Okta, the user is redirected back to PowerClerk. Alternatively, a program can provide a custom URL that the user will be used instead of PowerClerk’s front page.
Configuring SSO for use with multiple PowerClerk Programs
PowerClerk supports multiple IDPs from the same directory, so that you can use SSO with more than one PowerClerk program. Specifically, PowerClerk does not require the login page of a specific program to unconditionally redirect to the page starting the IdP-initiated login. If you use the same EntityID for both programs, you must also use the same Certificate for both programs.
Individual/unique Certificates and EntityIDs can also work. Your IDP should be running in IDP-initiated mode. Note that if you want to be able to login by clicking anything in PowerClerk (which in SAML terminology is the Service Provider == SP), SP-initiated MUST also be enabled.
Using Azure AD as an example:
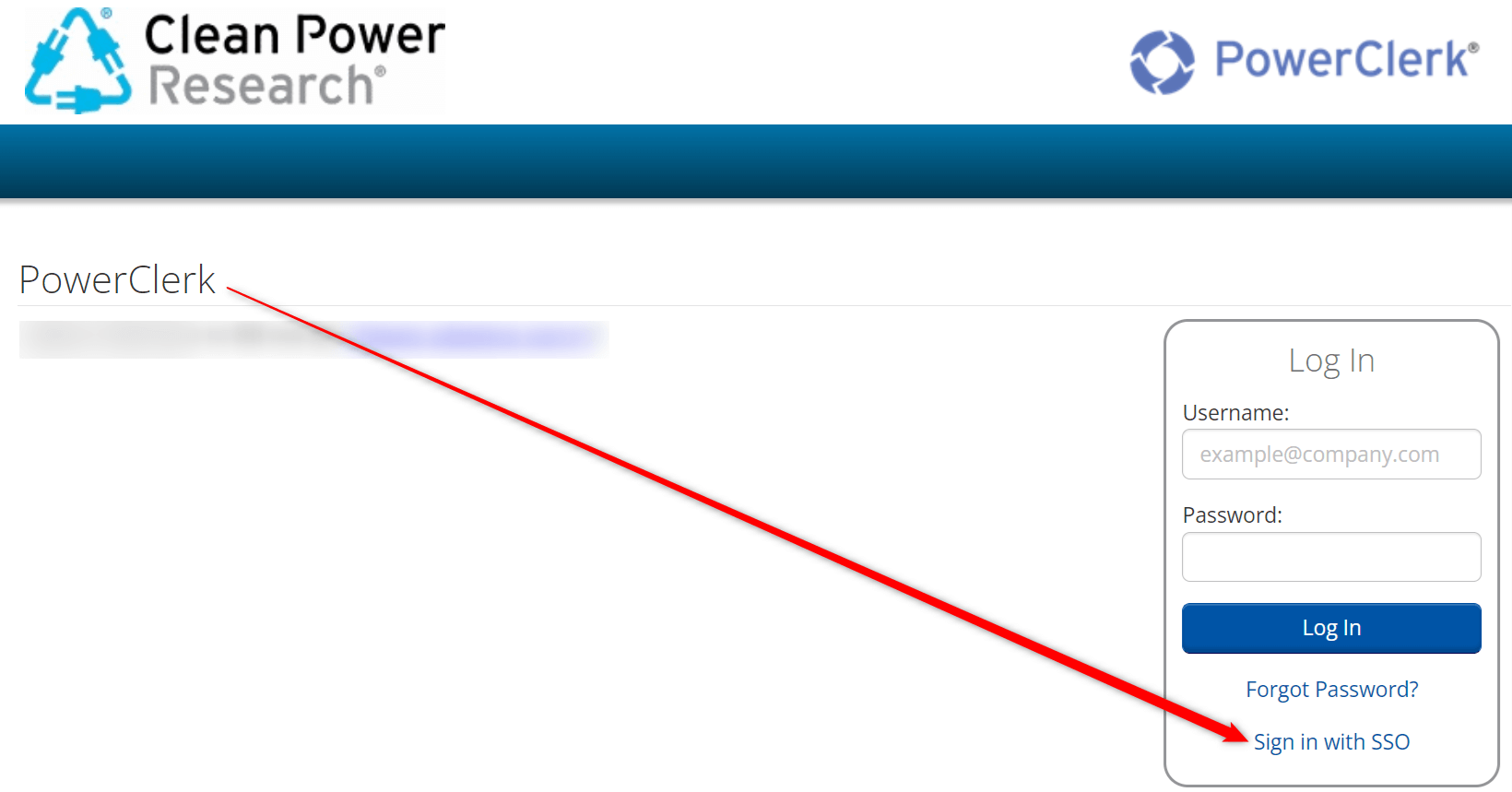
In addition to CPR requiring the Login URL (i.e. SignOnURL), Azure AD Identifier (i.e. EntityID), and Certificate for each PowerClerk Program, we will also need the User Access URL from you, which is what we use as the redirect URL for PowerClerk. Allowing CPR to configure your redirect URL on our end will prevent the user from being booted back to the login page (when switching between programs) where they would be forced to click the “SSO” hyperlink to log into the 2nd program (see image below):
Configuring the redirect URL removes this intermediate step and allows the switching between programs to be seamless from a UI perspective, to mimic how it works without using SSO, when using the “Change Program” drop-down menu inside PowerClerk:
Please note that the “User Access URL” is found outside of the SSO configuration and in the IDP app properties itself. To find the “User Access URL”, follow these steps for Azure (other IDPs will differ):
- Navigate to Azure Enterprise apps and click the app that has the User Access URL (e.g. this should be the name of your PowerClerk program):
 Figure 11: Azure Enterprise apps
Figure 11: Azure Enterprise apps - Then click “Properties” on the left-hand panel:
 Figure 12: Azure Enterprise apps – Properties
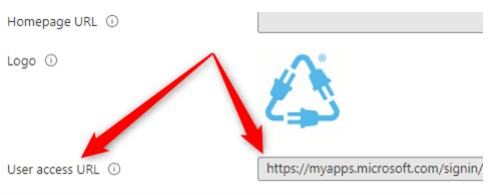
Figure 12: Azure Enterprise apps – Properties - On the right side, the User Access URL will be shown for apps with SSO configurations:
IDP Configuration Troubleshooting
To troubleshoot your IDP configuration, there are extensions available, such as the Chrome “SAML Tracer” extension, which is a tool for viewing SAML and WS-Federation messages sent through the browser during single sign-on and single logout. Such SAML tracer will let you watch what claims are sent when you go to login to PowerClerk, which would look similar to the below:
If you are having trouble getting your IDP configuration to work, plan on reaching out to your PowerClerk support representative (or support@powerclerk.com) to work through the following steps:
- Step 1: Send us a screenshot of your IDP configuration, so we can cross-check what you have configured in terms of the Entity ID, Reply URL, etc.
- Step 2: Send us a screenshot of the SAML error message you are receiving and attach the SAML Response and SAML Request .xml files.
- Step 3: If possible, create an account in your IDP and send us the credentials so that we can login to further troubleshoot your configuration.
- Step 4: CPR will set up a screenshare session with you to go over the configuration.
FAQs
- SP initiated: click the “Sign in with” SSO link on the PowerClerk login page
- IDP initiated: log into your IDP, click the link, and you're in PowerClerk
Have additional questions? Contact us to nominate your FAQ and help others find answers to your own questions concerning this feature.
Create A Support Ticket
Not finding your answer here? Submit a question to our support team at the PowerClerk Ticket System and leverage the PowerClerk team’s expertise.